The health crisis that’s been affecting the world since the beginning of the year has unfortunately come with a series of cyberattacks: public administrations, businesses, local authorities and even hospitals. No one has been spared (although some ransomware operators claim that they will show some respite…).
Email, which is the main means of workplace communication, is booming as a consequence of lockdown and widespread remote work. Everyone uses it. Everyone can be reached by email. All business documents go through mail – invoices, contracts, client information, documents, appointments. As a result, email is a victim of its own success: it is hackers’ target of choice when attacking organisations.
So, what do these attacks look like? How can we spot them and how can we protect ourselves against them?
Is spam still an issue?
If Bill Gates’ prediction had come true, the internet would be spam-free since 2006. A quick look into your spam folder should be enough to prove otherwise.

“Three million spam messages are sent on the internet every second – i.e. 262 billion spam messages every day, which accounts for 95,000 billion messages per year throughout their short lifetime (creation, sending, reception, storage and reading)” Les Echos Solutions, November 2019.
To many of us, spam emails stick out like a sore thumb and the ruses they use are so obvious that we do wonder why they still work. How, in the year 2020, can anyone still fall for the long-lost uncle suddenly wanting to leave you his immense fortune in inheritance? Unfortunately, many people do. “Spam is becoming an increasingly successful attack vector, with click rates rising from 13.4% in the second half of 2017 to 14.2% in 2018,” Adam Sheehan, Behavioural Science Lead at MWR InfoSecurity told The Economic Times.
Spam is still going strong for three key reasons:
- It costs next to nothing to send and it can bring huge profits. Sending one million emails costs from €5 to €4,000 and can bring up to €130,000 per month in revenue (L’Obs, 2016).
- There’s no single source. No organisation controls email. There’s no valve to stop the flooding. One spam message may be blocked by one mail provider but cleared by another one.
- Identifying an email message as spam isn’t easy and can be subjective. An ad may be perceived as spam by some people but not by others (that’s where antispam aggressiveness comes in).
[As an aside if you’re looking for quarantine entertainment, you might want to try answering spam messages]
The issue of spam itself can be quickly resolved by aggressive antispam filters, and deleting messages may be enough to forestall attacks – although aggressive antispam filters can block legitimate messages. But spam can become a serious threat for you and your business… when it contains malware.
Phishing, malware and ransomware
The starting point is spam. Somewhere in the midst of all the unsolicited messages, traps are hiding. What for? To trick message recipients into believing that the message is something important that they need to respond to – e.g. a bank request or a note from a colleague – and lure them into clicking a link or downloading an attachment. That’s called (spear)phishing. Vade Secure, an email security specialist who works with BlueMind, has published an infographic aimed at helping people spot such emails.
The attachment – when it is downloaded — or the link lead to malware. This includes Trojan horses. Once they’re installed or run, they can siphon all your system data. Some more aggressive programs might even open your system to remote control.

One type of frequently-talked about malware is ransomware. Ransomware encrypts the data on a victim’s computer and the hackers demand a ransom for its release. Victims receive payment instructions in exchange for the decryption key. Costs may range from a few hundred to thousands of Euros – typically in Bitcoins –, payable to the cybercriminals, and the consequences are often devastating.
Office 365 users are an ideal target for such attacks, as Vade Secure explain on their blog: “With 155 million corporate users and a single point of entry into the entire Office 365 suite, it’s a remarkably fertile environment for malicious behaviour. In contrast, before this service was available, each organisation had its own email server, and thus had to be hacked individually. Now, Office 365 presents one target: find a way in and hackers potentially have access to 155 million accounts!”
The old SaaS v. On Premises debate is less relevant here – not as much as your solution’s sovereignty.
You can protect yourself from cyberattacks with security tools (firewall, encrypting, two-factor authentication, backups, etc.). Some solutions go even further and use artificial intelligence, for example, to analyse the URLs contained in emails, attachments or images (e.g. appropriated logos). Still, one of the most effective actions you can take is to train your employees to spot threats, as the human factor represents the greatest risk.
The human factor
Technology alone isn’t enough to fight against email security threats.
With this analogy, CSO Online illustrates how the human risk weighs on cybersecurity: “Consider a footpath that diverges at a 90-degree angle, but there is a grassed area that fills the space of that right angle. Where are the majority of pedestrians going to walk? I can assure you that they will not be taking the longer route on the concrete footpath. There will be a well-worn dirt track through the middle of the grass. The fastest and easiest way to get where they need to get to. The same principle applies to security controls. When an end-user identifies an easier way to achieve their aims, then that is the route they will take. When security controls and technology solutions are implemented with minimal consideration for the workflows of the end-user, friction occurs. Where friction occurs, circumvention will inevitably be the result. Circumvention of security controls, of course, leads to data breaches.”
This is what BlueMind is working on – to meet users’ needs while incorporating security issues into its product development philosophy. Meeting user satisfaction – e.g. allowing and providing seamless access to the market’s email clients such as Outlook, Thunderbird, webmail, MacOS, mobile devices, etc. – helps prevent unplanned uses which could compromise your organisation’s security.
For instance, user circumvention often is an issue when it comes to passwords. No one is capable of memorising a dozen different 10-character long passwords. So, to save time, and despite corporate directives, people use their date of birth or their cat’s name and they use the same for all services. A required update? Why not use and old password you remember?!
Hackers are all too aware of this. Regardless of technological security levels, people are still the weak link and hackers’ main target. Human behaviour is an opportunity for them to exploit, and it represents a huge risk for organisations. This is why, in the last few years, cyberattacks have focused on people rather than infrastructure.
New employees, for instance, are their target of choice. Professional social media help hackers find out who has joined a company and when, in what role, in what team and under whose management. “The first weeks at a new job is a vulnerable time for employees. Depending on the role, it can be unclear to a new employee what is and isn’t typical, especially when it comes to processes and colleagues.” Vade Secure’s blog points out.
To contain human-related risks, a good cybersecurity strategy must at a minimum involve an internal awareness campaign – to communicate procedures and good practices clearly to employees as soon as they join, as well as throughout their evolution within the company. To deter circumvention, cybersecurity must be an integral part of corporate culture. It must not be presented as a constraint but as standard practice.
New human-centred threats
You have to hand it to hackers, they are resourceful. The Covid-19 pandemic is an ideal breeding ground for their creativity. Many cybersecurity companies are warning of an increase in attacks using the pandemic as bait in phishing campaigns (TechCrunch March 2020).
What these hackers do is called social engineering – the art of using human psychology rather than technology to design cyberattacks. For instance, rather than look for software weaknesses, they might call a company employee and impersonate an IT support colleague to try and lure them into giving them their password.
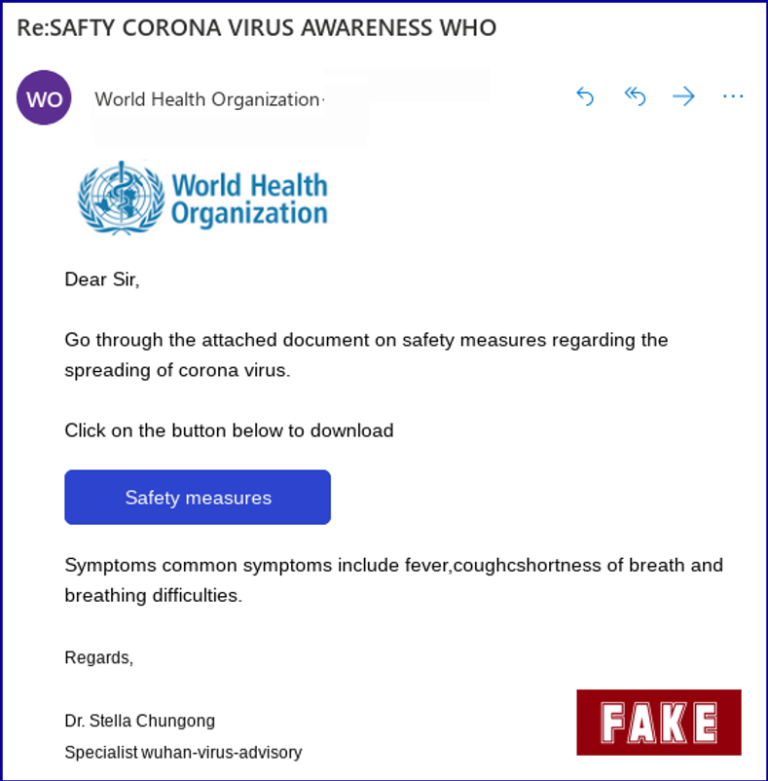
Riding the current pandemic wave, cybercriminals sent an email posing as WHO with a link to a document allegedly outlining Covid-19 prevention measures. In fact, the link redirected victims to a malicious webpage which attempted to collect identification details. The email contained several format and grammatical errors which were obvious giveaways to most people, but others – many – clicked the link anyway (you can find all the details about this scam here).
Social engineering can come in many shapes en forms. A particularly effective and dangerous one is BEC (Business Email Compromise). Have you seen the film “Thank you for calling” (Trailer)? It tells the story of Gilbert Chikli, a crook made famous by the “fake CEO” scam. “For 18 months, between 2005 and 2006, he passed himself off as the CEO of major French companies such as La Poste, Galeries Lafayette, Disneyland Paris, Pages jaunes or Caisse d’épargne, contacting company executives and talking them into handing him hundreds of thousands of Euros in cash or by bank transfer allegedly to fight terrorist financing and acting on the orders of the French secret services, thereby swindling almost 50 million Euros” (Wikipedia.fr).
This phone scam caused a big stir at the time — to the point it was made into a feature film –, but the concept having now moved to email — as Business Email Compromise –, it continues to cause major damage (in 2019, an Italian company was swindled out of $18.6 million in one week).
A BEC attack begins with identity theft whereby hackers pose as a company’s manager, CEO or supplier. They contact one or several company employees with the privileges necessary to respond to their demands and order a seemingly legitimate payment. The email message appears authentic and comes from a known authority figure, so the employee complies. Typically, the hacker will ask for the payment to be made by bank transfer or cheque, depending on the company’s usual policy. There have also been recent cases of sensitive data being demanded as payment instead of money.
Technology isn’t enough to fight such attacks! Employee training and awareness is key. Security specialists also recommend using multi-factor authentication, such as a combination of passwords and biometric data, in order to block hackers.
Security and BlueMind
BlueMind is a mail software publisher with strong security expertise. However, developing antivirus or antispam software is a business in its own right, which is why we rely on our partners for these solutions — Vade Secure and AltoSpam, for instance.
In parallel, we’ve taken a series of measures to make BlueMind secure. This includes:
- Trusted, up-to-date system components (postfix, Cyrus, postgreSQL, etc.),
- A built-in firewall that restricts data flows to authorised BlueMind users and components
- Encrypted data flows
- Modules such as password management
Certificate management
For increased, easier security, BlueMind uses advanced certificate management to encrypt internal and external exchanges. Certificates are configured in the admin console, which makes it transparent throughout the BlueMind infrastructure.
BlueMind server connections are secured via certificate. On single-server installations, the certificates generated when BlueMind is installed can be replaced by customised certificates.
Mail protocol encryption
By default, BlueMind supports standard mail encryption protocols – IMAPS, POPS and SMTP TLS.
The BlueMind solution uses standard mail protocols and recommends the use of their encrypted versions. The use of secured versions (IMAPS, POPS…) can be forced. SMTP negotiation also includes the STARTTLS option (SMTPS). All collaborative connections — between smartphones and BlueMind, between Outlook and BlueMind — and internet connections — via BlueMind’s web interfaces or the Thunderbird plugin — use the authentication-based (secure) HTTPS protocol.
Encryption is made via a signed certificate – which we recommend you replace by a trusted signed third-party certificate.
Built-in firewall
To protect your servers, BlueMind incorporates a firewall automatically configured to restrict data flows to those required and authorised hosts only.
Complex password policy
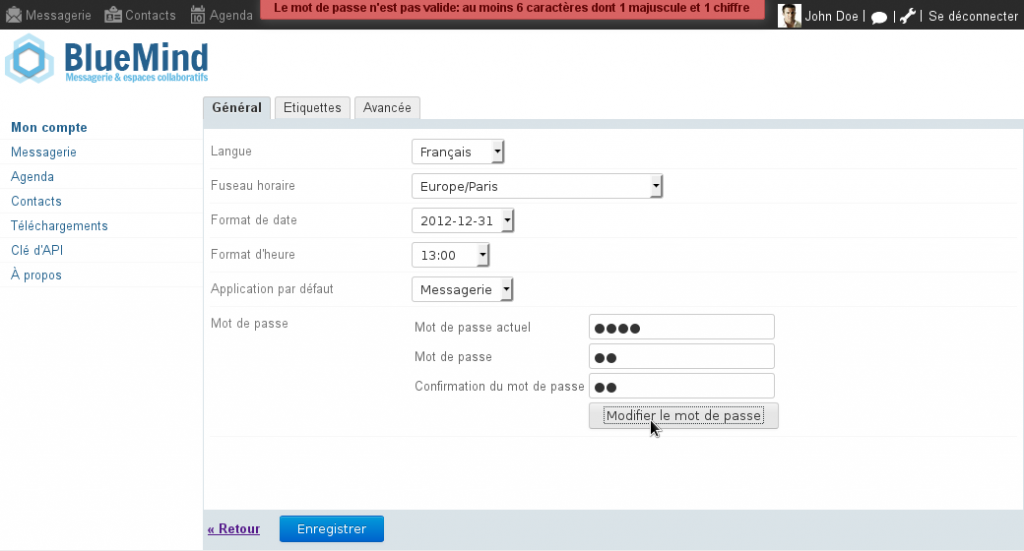
For extra user password security, you can set up a policy using the “Password SizeStrength” plugin which enforces strict rules for passwords to be valid. If a user does not comply with rules when they try to change their password, an alert is displayed at the top of the page.
Extra Security Measures
As part of a specific project, extra security measures can be taken, such as:
- A white list of authorised IPs, distributed by protocol,
- A list of ActiveSync-authorised devices.
Other infrastructure or flow-based security policies – e.g. a traffic analysis tool (an Intrusion Detection System such as Snort) – can also be set up to detect or react to suspicious activity.
BlueMind security breach handling
BlueMind takes great care to equip its solution with the highest security levels. A set of development rules is designed to limit security breaches. Although they are rare, breaches to the BlueMind code do occasionally occur. As soon as one is detected, it is analysed to establish its criticality. It is then corrected and a fix is released, either as part of minor version update if its criticality is low, or as a hotfix if its criticality is high.
In conclusion
Email is a great work tool, but it also is a preferred means of attack because of its ubiquity. Cybercriminals’ ingenuity knows no bounds. We recommend that you approach an email security specialist such as Vade Secure who will ensure that you are up to date with new fraudulent techniques and will help you implement the technological means required to counter them.
On your end, raising employee awareness is crucial, not as a one-off measure but continuously over the long term. It has to be integrated into your work culture.
During this time of massive remote work, you might be interested in reading ZdNet’s article “Working from home: cybersecurity for remote workers”.